Symmetric vs asymmetric encryption

Cryptographic data protection is an important field that's becoming increasingly relevant. The rapid development of blockchain technology based on cryptography has further expanded the scope of encryption's application. However, some people still argue over whether symmetric or asymmetric encryption is better. This article will tell you what symmetric and asymmetric encryption are, analyse their features and examine their differences, strengths, and weaknesses.
What is symmetric and asymmetric key cryptography?
Encryption, or cryptography, is a reversible transformation of information aimed to hide it from unauthorised persons while providing access to authorised users. Encryption provides 3 information security components:
- Confidentiality. Encryption conceals information from unauthorised users during transmission or storage.
- Integrity. Encryption is used to prevent information from being changed when being transmitted or stored.
- Identifiability. Encryption helps authenticate the source of information and prevent the information sender from denying that they were, in fact, the data's sender.
Encryption uses mathematical algorithms and keys. An algorithm is a set of mathematical operations required to perform a specific encryption process, while keys are strings of text and digits used to encrypt and decrypt data.
There are two main types of encryption — symmetric and asymmetric — which are distinguished by the type of keys used for encryption and decryption.
What is ssecymmetric encryption?
Symmetric encryption is the oldest encryption method known to humanity. For almost the entire history of cryptography, which dates back about 4,000 years, it was the only method of encrypting information.
Symmetric encryption defined
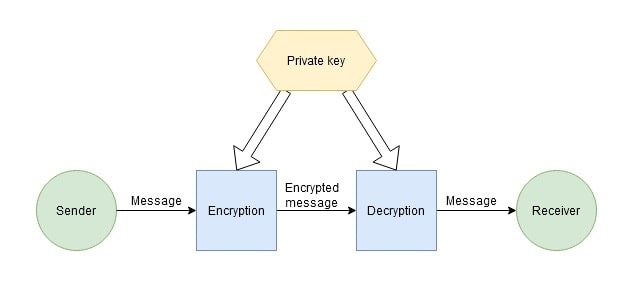
Symmetric encryption, also called private key encryption, is when data is encrypted and decrypted by the sender and recipient using the same secret key. This means that the key must be passed securely so that only the recipient can access it.
How does symmetric encryption work?
Here's how the process of protecting information through symmetric encryption works:
- The sender (or recipient) chooses an encryption algorithm, generates a key, informs the recipient (or sender, as the case may be) of the selected algorithm, and sends the key via a secure communication channel.
- The sender encrypts the message using the key and sends the encrypted message to the recipient.
- The recipient receives the encrypted message and decrypts it using the same key.
Types of symmetric key cryptography
There are two main types of symmetric cyphers: block and stream.
In block encryption, information is divided into blocks of fixed length (for example, 64 or 128 bits). These blocks are then encrypted one by one. The key is applied to every block in a prescribed order. That generally implies several cycles of mixing and substitution. The block cypher is an important component of many cryptographic protocols and is widely used to protect data transmitted over a network.
Each original character is converted to an encrypted one in a stream cypher, depending on the key used and its location in the original text. Stream cyphers have a higher encryption speed than block cyphers, but they also tend to have more vulnerabilities.
Symmetric key cryptography algorithms
There are quite a few symmetric cyphers. Here are some of the most famous examples.
Block cyphers:
- DES (Data Encryption Standard) is an encryption algorithm developed by IBM and approved by the US government in 1977 as the official standard. The block size for DES is 64 bits. Currently considered obsolete and unused.
- 3DES (Triple DES) was created in 1978 based on the DES algorithm to eliminate the main drawback of the latter: the small key length (56 bits), which can be cracked by brute force. The speed of 3DES is three times slower than that of DES, but the cryptographic security is much higher. The 3DES algorithm is based on DES, so it's possible to use programmes created for DES to implement it. It's still used, particularly by the electronic payment industry, but is gradually being replaced by newer algorithms.
- AES (Advanced Encryption Standard). This encryption algorithm with a 128 bits block size and a 128/192/256-bit key was developed in 2001 as a replacement for DES. It's currently considered one of the most efficient and secure symmetric cyphers and is therefore widely used.
- IDEA (International DATA Encryption Algorithm) is an algorithm developed in 1991 by the Swiss company Ascom. It uses a 128-bit key and a 64-bit block size. Although it is now also considered obsolete, it's still in use.
Stream cyphers:
- RC4 (Rivest cypher 4) was an algorithm developed in 1987 by the American company RSA Security. It became popular due to the simplicity of its hardware and software implementation and high algorithm speed. It's currently considered outdated and not secure enough but is still in use.
- SEAL (Software-optimised Encryption Algorithm) was developed in 1993 by IBM. The algorithm is optimised and recommended for 32-bit processors. It's one of the fastest cyphers and is considered very secure.
The strengths and weaknesses of symmetric key cryptography
The most notable advantage of symmetric encryption is its simplicity, as it uses a single key for both encryption and decryption. As such, symmetric encryption algorithms are significantly faster than asymmetric ones and require less processing power.
At the same time, the fact that the same key is used for encryption and decryption is the main vulnerability of symmetric encryption systems. The need to transfer the key to the other party is a security vulnerability because, if it falls into the wrong hands, the information will be decrypted. Accordingly, special attention should be paid to possible ways of intercepting the key and enhancing transmission security.
What is asymmetric encryption?
Asymmetric encryption is a relatively new cryptographic system that emerged in the 1970s. Its main goal is to fix the vulnerability of symmetric encryption, i.e., the use of a single key.
Asymmetric encryption defined
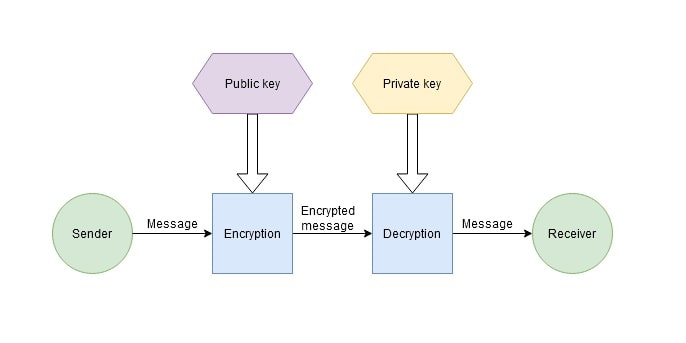
Asymmetric encryption, also called public key encryption, is a cryptographic system that uses two keys. The public key can be transmitted over an unsecured channel and is used to encrypt the message. A private key known only to the recipient is used to decrypt the message.
The pair of keys are mathematically related to each other, so you can calculate the public key by knowing the private one, but not vice-versa
How does asymmetric encryption work?
Here's how asymmetric encryption works:
- The recipient chooses an encryption algorithm and generates a public and a private key pair.
- The recipient transmits the public key to the sender.
- The sender encrypts the message using the public key and sends the encrypted message to the recipient.
- The recipient receives the encrypted message and decrypts it using their private key.
Asymmetric key cryptography algorithms
Examples of well-known asymmetric encryption algorithms include:
- RSA (Rivest Shamir Adleman), the oldest asymmetric encryption algorithm, was published in 1977 and named after its creators, American scientists from the Massachusetts Institute of Technology (MIT) Ron Rivest, Adi Shamir and Leonard Adleman. This is a relatively slow algorithm often used in hybrid encryption systems in combination with symmetric algorithms.
- DSA (Digital Signature Algorithm) was created in 1991 by the National Institute of Standards and Technology (NIST) in the United States. It's used for digital signature authentication. An electronic signature is created with a private key in this algorithm but can be verified with a public key. This means that only the signature owner can create the signature, but anyone can verify its authenticity.
- ECDSA (Elliptic Curve Digital Signature Algorithm) is a public key algorithm for creating a digital signature. This is a variant of DSA that uses elliptic curve cryptography. ECDSA is used on the Bitcoin network to sign transactions.
- Diffie–Hellman was published in 1976 by the American cryptographers Whitfield Diffie and Martin Hellman. It's a cryptographic protocol that allows two or more parties to obtain a shared private key using an unsecured communication channel. The key is used to encrypt the rest of the exchange using symmetric encryption algorithms. The scheme for distributing keys through secure channels proposed by Diffie and Hellman was an important breakthrough in cryptography since it removed the main problem of classical cryptography, key distribution.
The strengths and weaknesses of asymmetric key cryptography
The most obvious benefit of this encryption type is its security since the private key doesn't need to be passed on to anyone. Of course, this greatly simplifies key management in larger networks.
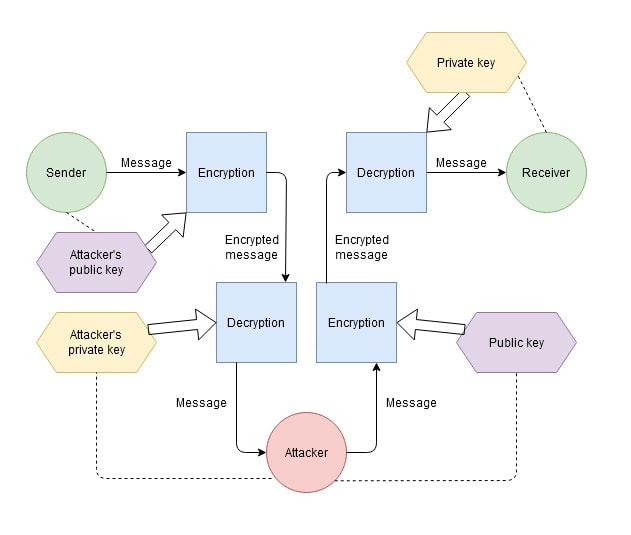
However, this encryption method also has drawbacks. The higher complexity, lower speed and higher demand for computational resources is one example. In addition, despite the high security of asymmetric encryption, it's still vulnerable to a man-in-the-middle attack (MITM), in which an attacker intercepts the public key sent by the recipient to the sender. The attacker then creates their own key pair and 'masquerades' as the recipient by sending a false public key to the sender that the sender thinks is the public key sent by the recipient. The attacker intercepts encrypted messages from the sender to the recipient, decrypts them with their private key, re-encrypts them with the recipient's public key, and sends the message to the recipient. In this way, none of the participants realises that a third party is intercepting the message or replacing it with a false one. This highlights the need for public key authentication.
Hybrid encryption
Hybrid encryption isn't its own encryption method like symmetric and asymmetric encryption are. Instead, it's a combination of both methods. These encryption systems first use asymmetric key algorithms for authenticating and transmitting a symmetric key. After that, the symmetric key is used to encrypt a large amount of data quickly. This kind of encryption system is particularly used in SSL/TLS certificates.
The difference between symmetric and asymmetric encryption
The main difference between symmetric and asymmetric encryption is using a single key versus a pair of keys. The other differences between these methods are merely consequences of this main difference.
Symmetric and asymmetric key cryptography compared
A comparison of symmetric and asymmetric key cryptography
Symmetric encryption | Asymmetric encryption |
One key is used to encrypt and decrypt data. | A key pair is used for encryption and decryption: the public and private keys. |
A simpler encryption method since only one key is used. | Since a key pair is used, the process is more complicated. |
Provides faster performance and requires less processing power. | It's slower and requires more processing power. |
Shorter keys (128-256 bits) are used to encrypt data. | Longer encryption keys (1024-4096 bits) are used. |
High complexity of key management. | Low complexity of key management. |
Used to encrypt large amounts of data. | Used when encrypting small amounts of data and providing authentication. |
Which is better: asymmetric or symmetric encryption?
The answer to the question depends on the specific problem that needs to be solved using encryption.
Symmetric algorithms are good for transferring large amounts of encrypted data. In addition, to organise a two-way data exchange using an asymmetric algorithm, both parties must know the public and private keys, or there must be two key pairs. Furthermore, symmetric algorithms' structural features make it much easier to modify them than asymmetric ones.
Asymmetric algorithms, on the other hand, are significantly slower. They do, however, improve data security by eliminating the possibility of an attacker intercepting the private key. Despite this, it remains vulnerable to man-in-the-middle attacks.
As you can see, the application areas for symmetric and asymmetric encryption are different, so you must always correlate the task at hand with the encryption algorithm when choosing one.
Tags
Try our Bitcoin Cloud Miner and get additional crypto rewards based on your trading volume. It's immediately available upon registration.
Try our Bitcoin Cloud Miner and get additional crypto rewards based on your trading volume. It's immediately available upon registration.



